Traffic Analysis with Wireshark
Links & Sources
Detecting Specific Behaviors
nmap scans
"TCP Flags in a nutshell..."
| Notes | Wireshark Filters |
|---|---|
| Global search. | - tcp- udp |
| - Only SYN flag. - SYN flag is set. The rest of the bits are not important. |
- tcp.flags == 2- tcp.flags.syn == 1 |
| - Only ACK flag. - ACK flag is set. The rest of the bits are not important. |
- tcp.flags == 16- tcp.flags.ack == 1 |
| - Only SYN, ACK flags. - SYN and ACK are set. The rest of the bits are not important. |
- tcp.flags == 18- (tcp.flags.syn == 1) and (tcp.flags.ack == 1) |
| - Only RST flag. - RST flag is set. The rest of the bits are not important. |
- tcp.flags == 4- tcp.flags.reset == 1 |
| - Only RST, ACK flags. - RST and ACK are set. The rest of the bits are not important. |
- tcp.flags == 20- (tcp.flags.reset == 1) and (tcp.flags.ack == 1) |
| - Only FIN flag - FIN flag is set. The rest of the bits are not important. |
- tcp.flags == 1- tcp.flags.fin == 1 |
TCP Scans
- Connect Scans
- SYN Scans
UDP Scans
ARP Poisoning / Spoofing
Manipulation of the "IP to MAC Address Table" via the sending of malicious ARP packets (MITM Attack).
ARP in a nutshell (THM)
- Works on the local network
- Enables the communication between MAC addresses
- Not a secure protocol
- Not a routable protocol
- It doesn't have an authentication function
- Common patterns are request & response, announcement and gratuitous packets.
| Notes | Wireshark filter |
|---|---|
| Global search | - arp |
| "ARP" options for grabbing the low-hanging fruits: - Opcode 1: ARP requests. - Opcode 2: ARP responses. - Hunt: Arp scanning - Hunt: Possible ARP poisoning detection - Hunt: Possible ARP flooding from detection: |
- arp.opcode == 1- arp.opcode == 2- arp.dst.hw_mac==00:00:00:00:00:00- arp.duplicate-address-detected or arp.duplicate-address-frame- ((arp) && (arp.opcode == 1)) && (arp.src.hw_mac == target-mac-address) |
Identifying between 2 spoofed packets is up to an analyst:
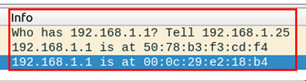
There are many ways to detect types of hosts in addition to IP and MAC addresses...
Traffic Types
- DHCP
- NetBIOS (NBNS)
- Kerberos
DHCP
DHCP investigation in a nutshell:
| Notes | Wireshark Filter |
|---|---|
| Global search. | - dhcp or bootp |
| Filtering the proper DHCP packet options is vital to finding an event of interest. - "DHCP Request" packets contain the hostname information - "DHCP ACK" packets represent the accepted requests - "DHCP NAK" packets represent denied requests Due to the nature of the protocol, only "Option 53" ( request type) has predefined static values. You should filter the packet type first, and then you can filter the rest of the options by "applying as column" or use the advanced filters like "contains" and "matches". |
- Request: dhcp.option.dhcp == 3- ACK: dhcp.option.dhcp == 5- NAK: dhcp.option.dhcp == 6 |
| "DHCP Request" options for grabbing the low-hanging fruits: - Option 12: Hostname. - Option 50: Requested IP address. - Option 51: Requested IP lease time. - Option 61: Client's MAC address. |
- dhcp.option.hostname contains "keyword" |
| "DHCP ACK" options for grabbing the low-hanging fruits: - Option 15: Domain name. - Option 51: Assigned IP lease time. |
- dhcp.option.domain_name contains "keyword" |
| "DHCP NAK" options for grabbing the low-hanging fruits: - Option 56: Message (rejection details/reason). |
As the message could be unique according to the case/situation, It is suggested to read the message instead of filtering it. Thus, the analyst could create a more reliable hypothesis/result by understanding the event circumstances. |
NBNS - NetBIOS Name Services
| Notes | Wireshark Filter |
|---|---|
| Global search. | - nbns |
| "NBNS" options for grabbing the low-hanging fruits: - Queries: Query details. - Query details could contain "name, Time to live (TTL) and IP address details" |
- nbns.name contains "keyword" |
Kerberos
| Notes | Wireshark Filter |
|---|---|
| Global search. | - kerberos |
| User account search: - CNameString: The username. Note: Some packets could provide hostname information in this field. To avoid this confusion, filter the "$" value. The values end with "$" are hostnames, and the ones without it are user names. |
- kerberos.CNameString contains "keyword" - kerberos.CNameString and !(kerberos.CNameString contains "$" ) |
| "Kerberos" options for grabbing the low-hanging fruits: - pvno: Protocol version. - realm: Domain name for the generated ticket. - sname: Service and domain name for the generated ticket. - addresses: Client IP address and NetBIOS name. Note: the "addresses" information is only available in request packets. |
- kerberos.pvno == 5- kerberos.realm contains ".org" - kerberos.SNameString == "krbtg" |
ICMP Tunneling
As it is a trusted network layer protocol, sometimes it is used for denial of service (DoS) attacks; also, adversaries use it in data exfiltration and C2 tunnelling activities...
- ICMP protocols afford opportunities to carry extra data.
- Indicators
- Large volumes of ICMP traffic
- Anomalous ICMP packet sizes
- Custom packets can still be made which match the standard ICMP packet size of 64 bytes...
| Notes | Wireshark filters |
|---|---|
| Global search | - icmp |
| "ICMP" options for grabbing the low-hanging fruits: - Packet length. - ICMP destination addresses. - Encapsulated protocol signs in ICMP payload. |
- data.len > 64 and icmp |
DNS Tunneling
- Indicators
- Longer queries than typical ones
- Crafted for subdomain addresses
- These are actually encoded commands
encoded-commands.malware.com
- These are actually encoded commands
| Notes | Wireshark Filter |
|---|---|
| Global search | - dns |
| "DNS" options for grabbing the low-hanging fruits: - Query length. - Anomalous and non-regular names in DNS addresses. - Long DNS addresses with encoded subdomain addresses. - Known patterns like dnscat and dns2tcp. - Statistical analysis like the anomalous volume of DNS requests for a particular target. !mdns: Disable local link device queries. |
- dns contains "dnscat"- dns.qry.name.len > 15 and !mdns |